What Happens When AI Tries to Mimic Protected Art?

Table of Links
-
Discussion and Broader Impact, Acknowledgements, and References
D. Differences with Glaze Finetuning
H. Existing Style Mimicry Protections
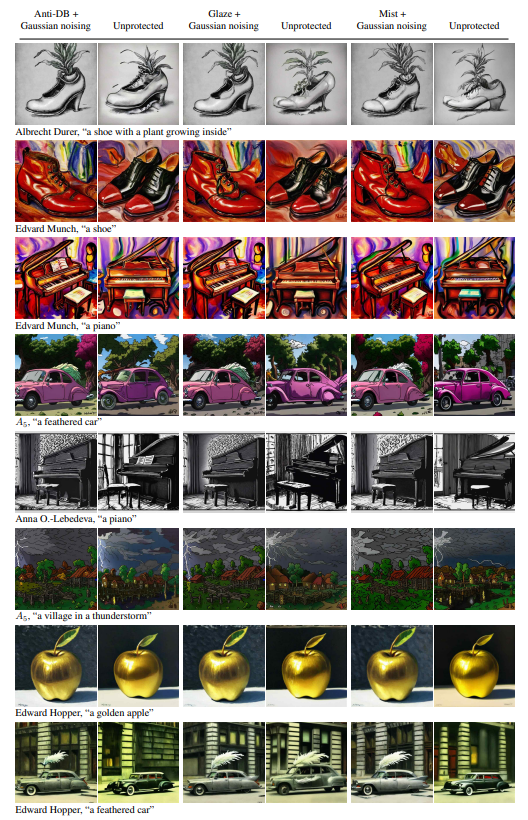
B Robust Mimicry Generations

\

\

\
\

\
:::info
Authors:
(1) Robert Honig, ETH Zurich (robert.hoenig@inf.ethz.ch);
(2) Javier Rando, ETH Zurich (javier.rando@inf.ethz.ch);
(3) Nicholas Carlini, Google DeepMind;
(4) Florian Tramer, ETH Zurich (florian.tramer@inf.ethz.ch).
:::
:::info
This paper is available on arxiv under CC BY 4.0 license.
:::
\









